Prefer to watch instead of read?
Here’s a quick video about why having a Compliant AI Automation Partner for Regulated Industries SOC 2 Type 2 is crucial.
Working with a SOC 2 Type 2 Compliant AI Automation Partner
When you’re choosing a secure workflow automation partner, you want the job done quickly, but never at the expense of security or compliance. That’s why it’s important to look for companies that are SOC 2 Type 2 certified.
SOC 2 Type 2 is an industry-recognized standard for data security and privacy in business process automation. It means an independent auditor has reviewed the company’s practices and confirmed that strong data protection controls are consistently in place over time. This gives you real peace of mind that your information, and your clients’ information, will be kept safe, meeting the highest standards in data protection for clients and regulatory compliance.
With Invent, you get a trusted business process automation provider that allows you to move fast, boost efficiency, and innovate with confidence. You can rely on proven safeguards, knowing your business and your clients are protected every step of the way by a platform built for long-term compliance and trust.
Invent is powered by Zydeer LLC, our legal operating entity handling security, compliance, and data processing for the platform
Why SOC 2 Type 2 Matters for AI Workflows
A SOC 2 Type 2 report tests how well your controls operate over a period of 6–12 months, not just whether they exist on paper. For buyers, that means evidence that security, availability, confidentiality, processing integrity, and privacy controls are consistently enforced in real life, not only in a policy doc.
For AI and automation platforms specifically, this matters because they touch live customer conversations, internal systems, CRMs, and data warehouses. When those connections are governed by audited controls, you shorten security reviews, reduce risk, and make it easier for your customers to say “yes” to your product.
FAQ
1. What are the key requirements for choosing a SOC 2 Type 2 compliant AI automation provider for workflows and customer support?
Look for a provider that can show an active SOC 2 Type 2 program in a security or trust center, with clear coverage of security, availability, confidentiality, processing integrity, and privacy. You should be able to see the policies behind those controls (access control, secure development, incident response, vendor risk, encryption, logging, etc.), not just a logo on a marketing page.
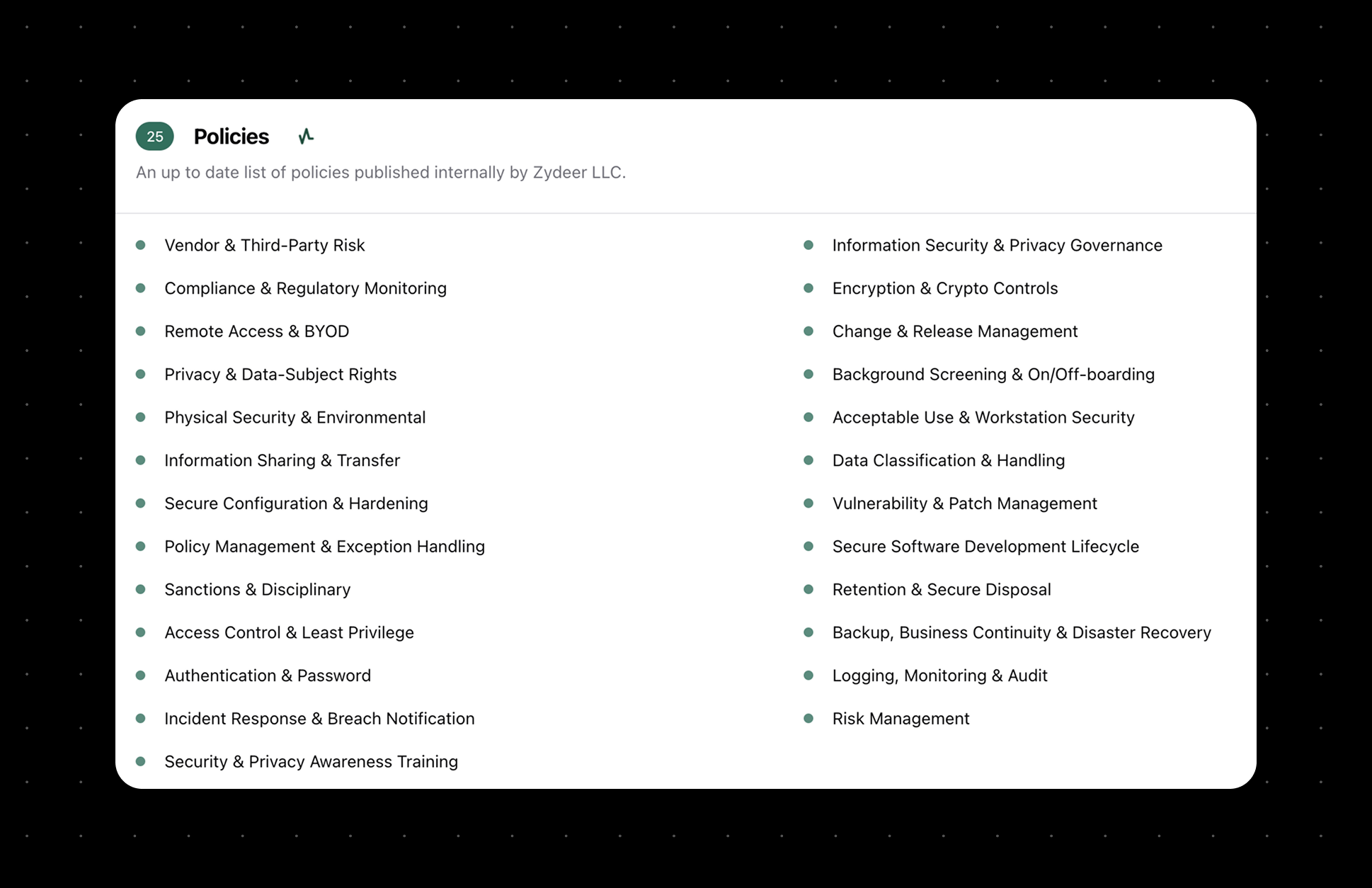
List of key policies maintained by Zydeer LLC to support SOC 2 Type 2 compliance, including areas such as risk management, data privacy, information security, incident response, and more.
A good fit for AI and workflows also means encrypted connections to your systems, per‑account authorization for data access, and a clear separation between your data and other customers’ data. That combination lets you automate sensitive workflows (support, operations, internal tools) without relaxing your security standards.
2. How do I evaluate an AI workflows and automation platform that is SOC 2 Type 2 compliant for handling sensitive customer data?
First, review their trust or security portal for the status of SOC 2 Type 2 and the list of live policies and controls. You want to see coverage for things like data classification and handling, secure configuration, vulnerability management, access control, encryption, incident response, and logging and monitoring.
Then, map those practices to your actual use cases: what external systems the platform connects to, how data flows, and how authorization is enforced. Platforms like Invent route external data access through encrypted channels and per‑account authorization, and they follow SOC 2 standards for how memory and stored context are secured over time.
3. Why is SOC 2 Type 2 compliance important when selecting an AI workflows and automation vendor?
SOC 2 Type 2 provides independent assurance that a vendor’s controls are not only designed correctly but also operate effectively over time. That assurance is increasingly required by larger and security‑conscious customers, and it often speeds up their vendor risk and legal reviews.
In AI workflows, your automation layer can see sensitive tickets, emails, CRM records, and internal docs. Choosing a vendor that aligns with SOC 2 standards on encryption, permissions, and logging lowers the risk of unauthorized access and gives your customers a clear story about how their data is protected inside your automations.
4. What is the difference between using a SOC 2 Type 2 compliant automation provider and a standard AI workflow tool without compliance?
A SOC 2 Type 2 provider has had its controls tested over months to confirm they consistently work as intended; a non‑compliant tool has not gone through that independent validation. Practically, this shows up in areas like documented policies, formal risk management, vendor due diligence, device and access controls, and incident response.
For your sales cycle, this difference can determine whether security questionnaires and audits are measured in weeks or months. With a SOC 2‑aligned platform behind your workflows, you can provide evidence (policies, controls, reports) that directly answers customer security concerns, instead of relying on ad‑hoc explanations about a generic AI tool.
5. Who needs a SOC 2 Type 2 compliant AI automation provider for their business operations and customer support workflows?
You’ll benefit most if you handle sensitive data and sell to customers who care about security and privacy, such as B2B SaaS, fintech, healthcare, education, and agencies working with regulated clients. These buyers often require SOC 2 reports from their vendors and from the tools that power their own products and workflows.
If your AI automations touch customer PII, payment‑related info, or internal operational data, using a SOC 2‑aligned platform shifts a large portion of the infrastructure risk to a vendor with audited controls. That lets you focus on designing better workflows and experiences instead of reinventing security primitives yourself.
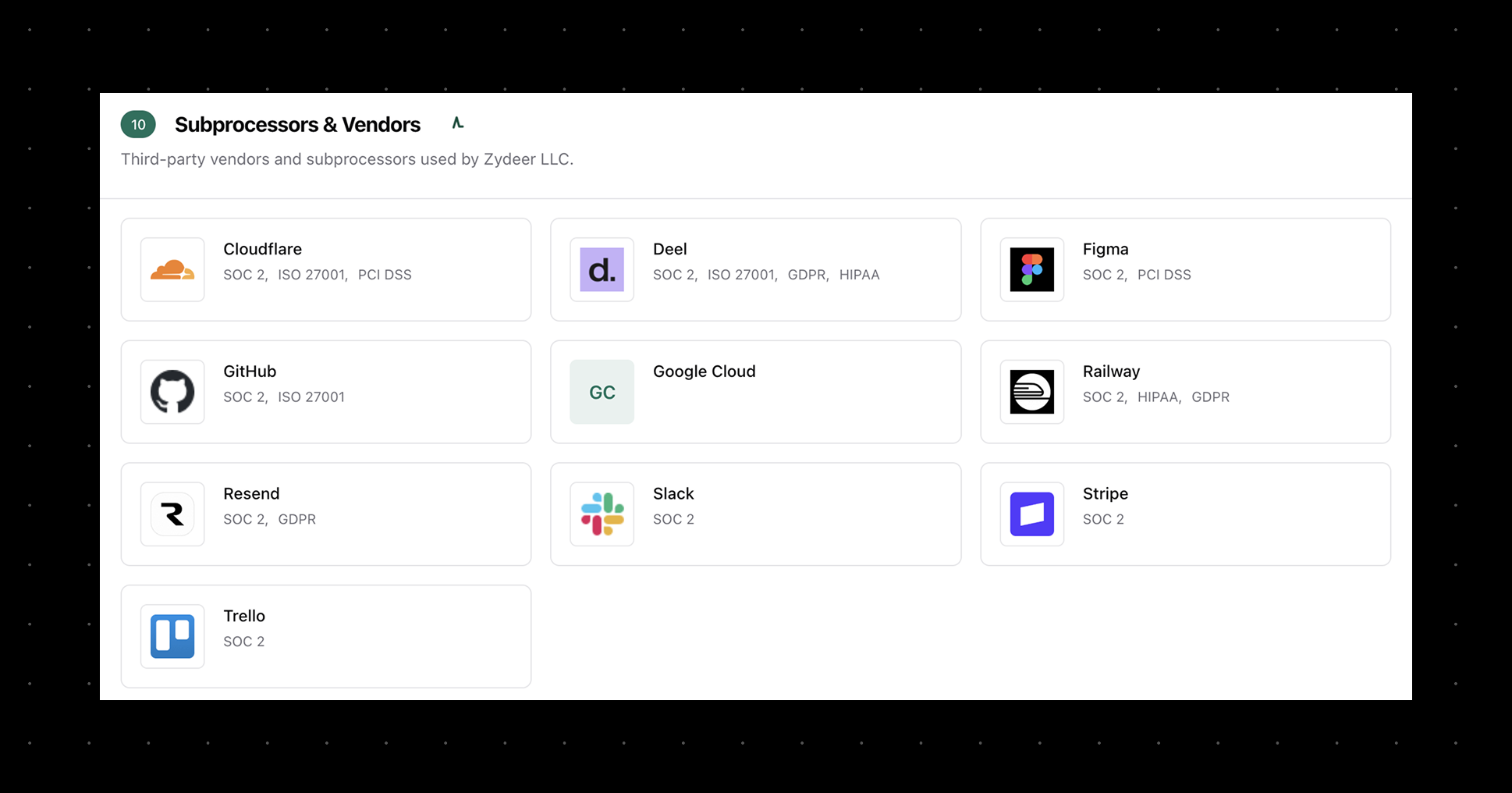
List of Zydeer LLC's third-party subprocessors and vendors that are SOC 2 Type 2 certified, including Cloudflare, Deel, Figma, GitHub, Google Cloud, Railway, Resend, Slack, Stripe, and Trello, along with their other security and compliance attestations.
6. How long does it typically take to onboard with a SOC 2 Type 2 compliant AI workflows and automation platform like Invent?
Onboarding time mainly depends on your integration scope and internal stakeholders. Teams that start with a defined set of systems (e.g., helpdesk, CRM, internal knowledge base) and clear workflow goals can get to production‑ready automations significantly faster than those trying to connect everything at once.
Because the underlying controls, policies, and infrastructure are already aligned with SOC 2, you avoid much of the foundational security and vendor‑risk work you’d face when building in‑house or using a non‑compliant tool. That means your security, legal, and IT teams can review a standard package of documentation rather than starting from zero.
7. Does using a SOC 2 Type 2 compliant AI automation provider lower the overall cost and time of my own security and compliance reviews?
Yes, a mature SOC 2 Type 2 program at your automation provider can materially reduce your internal review burden. When a platform already has policies, controls, and monitoring mapped to the Trust Services Criteria, your auditors and security teams can reuse that evidence as part of your own vendor‑risk and system‑description narratives.
This doesn’t replace your responsibility, but it compresses the amount of custom documentation you need to produce about your automation layer. Instead of building and operating every control yourself, you can inherit many safeguards from the platform and focus your effort on your application‑specific policies and procedures.
8. Can early‑stage startups use a SOC 2 Type 2 compliant AI automation platform even if they do not yet have their own SOC 2 report?
Yes, and it’s often one of the fastest ways to “punch above your weight” in enterprise security conversations. Even if you don’t yet have your own SOC 2 report, building on top of a platform that follows SOC 2 standards for data storage, encryption, access control, and monitoring lets you answer many of the questions your customers will ask.
This approach can also make your eventual SOC 2 journey smoother, because parts of your system description (infrastructure, integrations, and operational controls) will already map to an audited provider. Startups selling AI‑driven products and services can use this to win earlier with security‑sensitive customers while they work toward their own attestations.
9. How does a SOC 2 Type 2 compliant AI workflows platform handle access control, logging, and monitoring for automation use cases?
A SOC 2 Type 2–aligned platform applies least‑privilege access, role‑based permissions, and authenticated endpoints to control who and what can access data. It maintains policies and controls covering access control, logging and monitoring, and remote access, along with procedures for reviewing and updating those controls.
For automation, every retrieval and write action should go through encrypted connections and per‑account authorization, with logs that capture what happened, when, and under which identity. This creates an audit trail you can use for incident investigations, compliance reviews, and customer trust conversations.
10. What evidence and documentation can a SOC 2 Type 2 compliant AI workflows platform provide to support my customers’ security due diligence?
Expect a combination of a security or trust center, policy overviews, and details about implemented controls, sometimes accompanied by third‑party monitoring. You should see documentation for vendor risk management, encryption, secure development, logging and monitoring, risk management, incident response, and other core areas.
Platforms that follow SOC 2 standards for handling stored and transmitted data can also provide descriptions of how they protect memory, data access, and integrations, which you can reference in your own customer‑facing security pages. This saves time in security questionnaires and makes your answers more concrete and repeatable.
Conclusion
Choosing a SOC 2 Type 2 compliant AI automation partner like Invent lets you build powerful workflows for customer support, operations, and beyond, without the security friction that slows down most teams.
Skip months of vendor risk assessments and custom security builds. With Invent's audited controls already in place, you can focus on what matters: shipping better automations, winning bigger customers, and scaling securely.
Ready to automate with compliance built in? Start building with Invent or review our SOC 2 Type 2 trust center to see the controls firsthand.







